by Nikos Nikolaou (ITML)
With digital identity becoming part of everyday interaction, the importance of understanding Centralised and Decentralised Identity systems is growing[1][2]. Each model offers its own set of implications for user control, security, and trust.
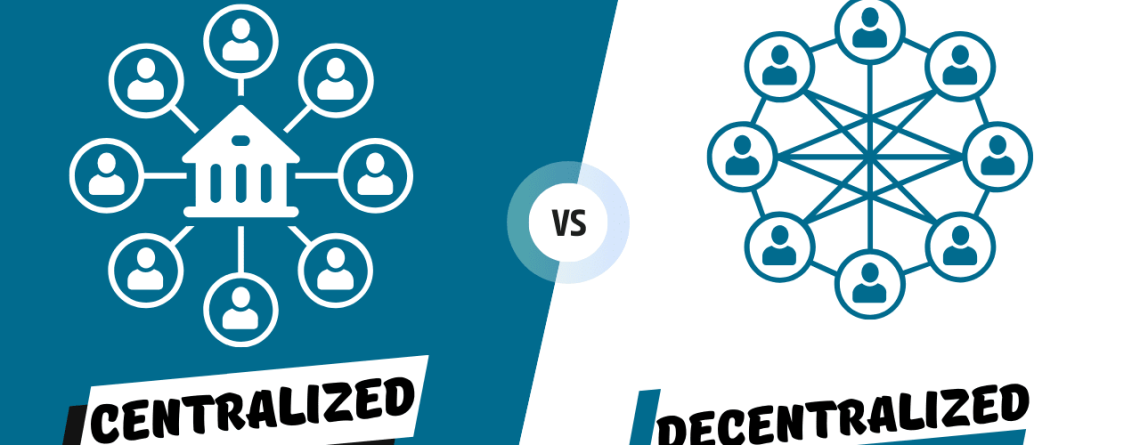
Centralised Identity Systems put the power of user data in the hands of a single authority that controls storage, access, and verification processes. This model is convenient and familiar but also concentrates a risk: user information becomes vulnerable to data breaches, misuse, and single points of failure that disrupt services or expose sensitive data. Because of being centrally controlled, there is limited choice but to place full reliance on identity verification with a centralised entity. This diminishes user autonomy and people’s capability of managing or controlling their own identities. Moreover, the lack of insight into how your own data is accessed and used can destroy any trust. These weaknesses highlight why Decentralised Identity models -where individuals regain control, privacy, and transparency- are increasingly seen as a more secure and user-centric alternative.
Decentralised Identity gives full control to users over their personal data by empowering them to decide precisely what information they will share and with whom. As a user-centric model, it enhances privacy and independence from a central authority in managing one’s own identity. On a blockchain, it enforces strong security and resilience because there is a reduction in the related risks of single points of failure[3]. Verification is done through decentralised, cryptographic proofs rather than traditional, centralised gatekeepers, enhancing trust and independence. Secondly, transparent and tamper-resistant data records facilitate accountability, which does not compromise users’ control. These characteristics make Decentralised Identity an influential alternative to traditional centralised systems.
The main question to answer when choosing between Centralised and Decentralised Identity models is: “Which model do I want for Identity Management?“[4]. The answer depends on a set of practical and strategic factors to be analysed before the final choice. These will include the size and complexity of digital environment, especially whether you operate in a layered or demanding Information Technology (IT) IT infrastructure that requires scalability. Consider the range of applications and systems in use; due to the variations within identity solutions themselves, the issues of compatibility and integration capabilities are of utmost importance. Security requirements also come into environments where security is a top priority. In that case, advanced features might be needed like multi-factor authentication or single sign-on. Of course, budget-related constraints should be considered because identity management solutions range from very expensive to inexpensive. Future growth plans should inform any decision to make sure the model is chosen and can scale effectively over time. In addition, user needs are important. The intuitiveness and access of the solution are vital, particularly when the working environment is characterised as a highly user-populated environment or with personnel with low technical skills.
CONSENTIS sets out to drive identity management beyond the current state of the art, fundamentally reconsidering how personal data is controlled, shared, and protected. Its ambition is to move from traditional, centralised approaches toward a more user-centric and privacy-preserving model. By combining the principles of (Self-sovereign identity) SSI and advanced Privacy-enhancing technologies (PETs), CONSENTIS envisions a decentralised identity ecosystem where the ownership of individual data continues to vest with the individual while organisations gain from secure, trustworthy, and scalable identity processes. This integrated approach sets the foundation for a next-generation framework improving security and enhancing privacy while supporting more transparent and resilient digital interactions.
[1] https://www.my1login.com/identity-explained/centralised-identity-management
[2] https://www.identity.com/decentralized-identity/
[3] https://www.sciencedirect.com/science/article/pii/S2665917424000084
[4] https://www.techtarget.com/searchsecurity/definition/identity-access-management-IAM-system